- Головна
- Готові шкільні презентації
- Презентація на тему «Computer or book. Pros and cons»
Презентація на тему «Computer or book. Pros and cons»
324
Слайд #1
COMPUTER vs BOOK
The presentation
was prepared by
Halyna Bilyk
The presentation
was prepared by
Halyna Bilyk

Слайд #2
Book for man
For details
Development of analytical skills and intuition
The mystery of the soul's
Information about readers
Learning about the world
For details
Development of analytical skills and intuition
The mystery of the soul's
Information about readers
Learning about the world

Слайд #3
ADVANTAGES:
1. Book much easier to read : it can take to the kitchen, the bathroom, in the bed, a walk in the park, on the beach, without fear that it will be damaged or stolen.книга
1. Book much easier to read : it can take to the kitchen, the bathroom, in the bed, a walk in the park, on the beach, without fear that it will be damaged or stolen.книга

Слайд #4
ADVANTAGES:
2 . Reading from a computer screen view port . Book in this sense - much more healthy way to get information
2 . Reading from a computer screen view port . Book in this sense - much more healthy way to get information

Слайд #5
ADVANTAGES:
3 . Is the best gift book - the question , of course, debatable, but it is still real. After all, does not come to mind is to give someone a birthday text file or a link to the site.
3 . Is the best gift book - the question , of course, debatable, but it is still real. After all, does not come to mind is to give someone a birthday text file or a link to the site.

Слайд #6
ADVANTAGES:
4 . The book can not become a victim of a computer virus or operating system failure
4 . The book can not become a victim of a computer virus or operating system failure

Слайд #7
Computer for man
Harms
Benefits
Harms
Benefits
Слайд #8
Benefits
Constant generation of new knowledge
Education in the home
Storage material required
Small footprint, but fullness can not replace one cabinet
Use in medicine
Use in trade
Constant generation of new knowledge
Education in the home
Storage material required
Small footprint, but fullness can not replace one cabinet
Use in medicine
Use in trade

Слайд #9
Harms (after prolonged use)
Impaired vision
Impaired vision

Слайд #10
Overvoltage hand joints and muscles of the forearm

Слайд #11
The disease of the musculoskeletal system Stagnation of blood

Слайд #12
The disease of the nervous system Computer addiction(mental disorders)

Слайд #13
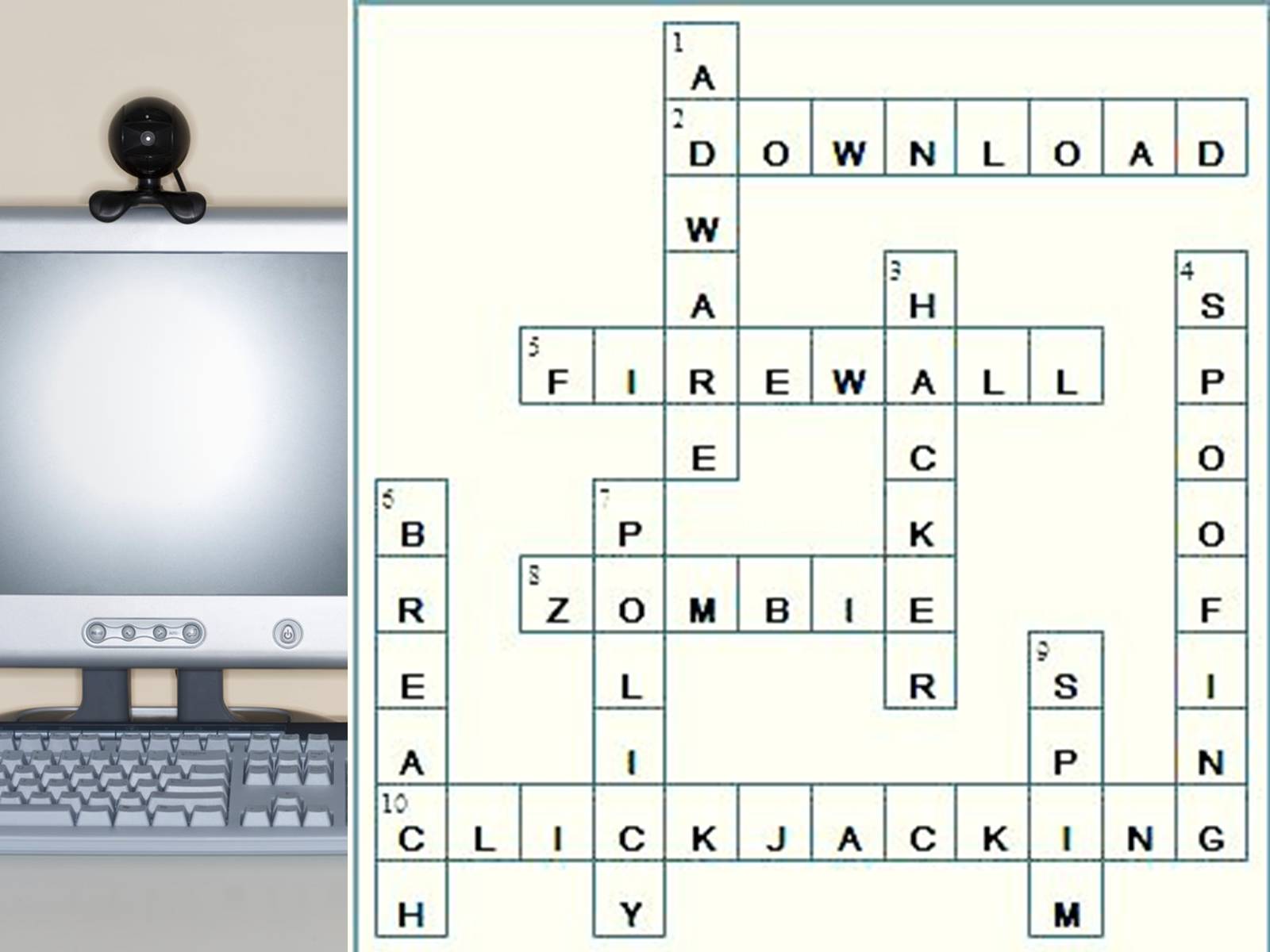
Crossword
Across
2. The transfer of data from one computer (or server) to another computer.
5.A security tool that protects an individual computer or even an entire network from unauthorized attempts to access your system.
8.A computer overtaken by a hacker and used to perform malicious tasks.
10.is a malicious technique of tricking Web users into revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages.
Down
1.A form of spyware that enters your computer from an Internet download.
3.A person who enjoys exploring the details of computers and how to stretch their capabilities.
4.Forging an e-mail or instant message address to make it appear as if it came from someone or somewhere other than the true source.
6.A violation or infraction, as of a law, a legal obligation, or a promise.
7.A course of action, guiding principle, or procedure considered expedient, prudent, or advantageous.
9.A new term for spam messages being sent to instant message addresses.
Across
2. The transfer of data from one computer (or server) to another computer.
5.A security tool that protects an individual computer or even an entire network from unauthorized attempts to access your system.
8.A computer overtaken by a hacker and used to perform malicious tasks.
10.is a malicious technique of tricking Web users into revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages.
Down
1.A form of spyware that enters your computer from an Internet download.
3.A person who enjoys exploring the details of computers and how to stretch their capabilities.
4.Forging an e-mail or instant message address to make it appear as if it came from someone or somewhere other than the true source.
6.A violation or infraction, as of a law, a legal obligation, or a promise.
7.A course of action, guiding principle, or procedure considered expedient, prudent, or advantageous.
9.A new term for spam messages being sent to instant message addresses.

Слайд #14
Crossword
Across
2. The transfer of data from one computer (or server) to another computer.
5.A security tool that protects an individual computer or even an entire network from unauthorized attempts to access your system.
8.A computer overtaken by a hacker and used to perform malicious tasks.
10.is a malicious technique of tricking Web users into revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages.
Down
1.A form of spyware that enters your computer from an Internet download.
3.A person who enjoys exploring the details of computers and how to stretch their capabilities.
4.Forging an e-mail or instant message address to make it appear as if it came from someone or somewhere other than the true source.
6.A violation or infraction, as of a law, a legal obligation, or a promise.
7.A course of action, guiding principle, or procedure considered expedient, prudent, or advantageous.
9.A new term for spam messages being sent to instant message addresses.
Across
2. The transfer of data from one computer (or server) to another computer.
5.A security tool that protects an individual computer or even an entire network from unauthorized attempts to access your system.
8.A computer overtaken by a hacker and used to perform malicious tasks.
10.is a malicious technique of tricking Web users into revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages.
Down
1.A form of spyware that enters your computer from an Internet download.
3.A person who enjoys exploring the details of computers and how to stretch their capabilities.
4.Forging an e-mail or instant message address to make it appear as if it came from someone or somewhere other than the true source.
6.A violation or infraction, as of a law, a legal obligation, or a promise.
7.A course of action, guiding principle, or procedure considered expedient, prudent, or advantageous.
9.A new term for spam messages being sent to instant message addresses.
Слайд #15
ADVANTAGES:
1. Information can be found on the Internet for free. A freebie, as you know , the best friend of the student.
1. Information can be found on the Internet for free. A freebie, as you know , the best friend of the student.

Слайд #16
ADVANTAGES:
2 . Electronic versions of books are indispensable when writing essays and diplomas. Press «Ctrl + C», then «Ctrl + V» is much easier than manually retype or scan . Although often falls to the student that simply finds the scientific work in finished form.
2 . Electronic versions of books are indispensable when writing essays and diplomas. Press «Ctrl + C», then «Ctrl + V» is much easier than manually retype or scan . Although often falls to the student that simply finds the scientific work in finished form.

Слайд #17
ADVANTAGES:
4 . Unlike printed with products on your computer , you can put your favorite font and a comfortable size . It is possible to use bookmarks , annotations , and hyperlinks .
4 . Unlike printed with products on your computer , you can put your favorite font and a comfortable size . It is possible to use bookmarks , annotations , and hyperlinks .

Слайд #18
ADVANTAGES:
5 . Electronic library not clutter the shelves and is not covered with dust.
5 . Electronic library not clutter the shelves and is not covered with dust.

Слайд #19
QUESTIONS
1. What are computer addicts like?
2. Have you ever used a computer? What do you use it for?
3. Why are computers used?
4. Why are more boys than girls interested in computers ?
3. Is computer addiction harmful?
1. What are computer addicts like?
2. Have you ever used a computer? What do you use it for?
3. Why are computers used?
4. Why are more boys than girls interested in computers ?
3. Is computer addiction harmful?

Слайд #20
QUESTIONS
1. What kind of books do you prefer to read?
2. Is it possible to live without books for you?
3. Books are our friends, aren't they?
1. What kind of books do you prefer to read?
2. Is it possible to live without books for you?
3. Books are our friends, aren't they?

Слайд #21
Computer and the book can not be compared.
And then, and another is an integral part of our life. And especially not to say that computers still win the book. At least in the near future, mankind has not exactly abandon books, developing, improving and printing, and computer technology.
And then, and another is an integral part of our life. And especially not to say that computers still win the book. At least in the near future, mankind has not exactly abandon books, developing, improving and printing, and computer technology.

Слайд #22
Thanks for watching
